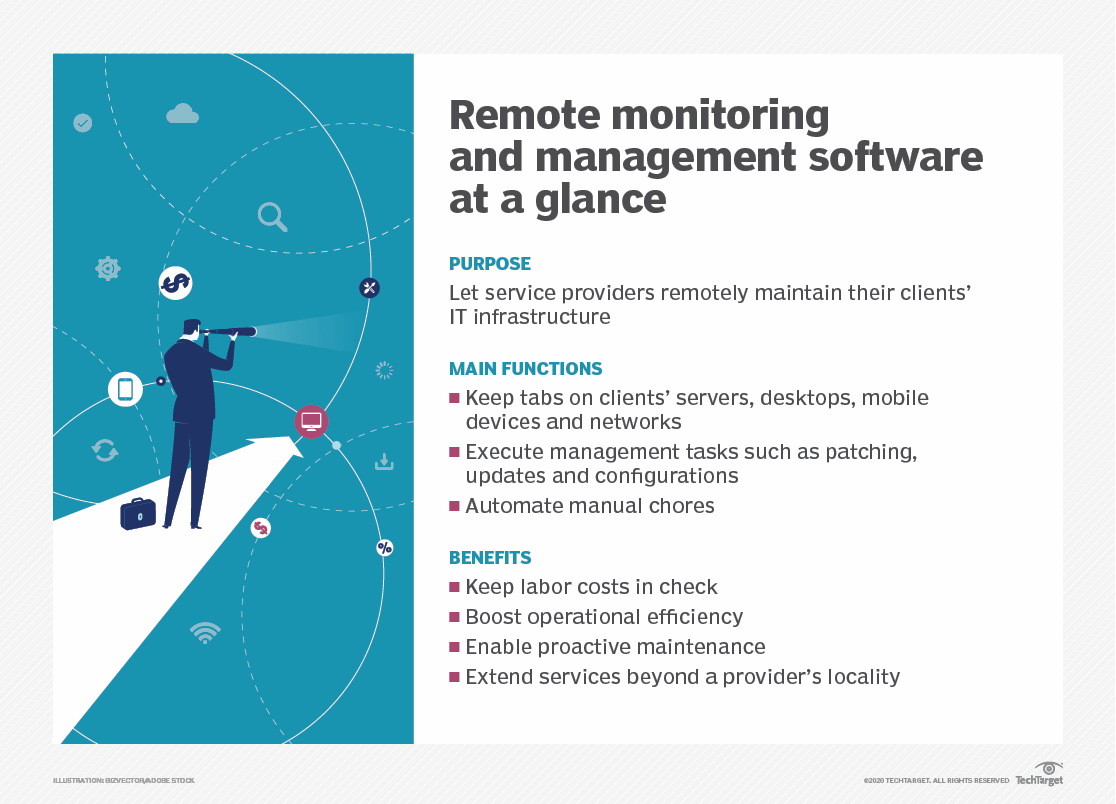
Rmm remote monitoring and management – RMM: Remote Monitoring and Management, is a powerful tool that empowers businesses to manage their IT infrastructure efficiently and effectively. RMM software offers a comprehensive suite of features, enabling IT teams to monitor devices, systems, and applications remotely, ensuring optimal performance and security.
Table of Contents
From proactive monitoring to automated tasks, RMM solutions provide valuable insights into system health, enabling timely intervention and preventing potential issues before they escalate. The ability to manage and control devices remotely simplifies IT operations, enhances productivity, and reduces the need for on-site visits.
Managing and Monitoring with RMM

RMM (Remote Monitoring and Management) tools empower IT professionals to remotely monitor and manage a wide range of devices and systems. These tools offer real-time visibility into the health and performance of IT infrastructure, enabling proactive problem resolution and improved efficiency.
Real-Time Monitoring of Devices and Systems
RMM tools provide a centralized platform for monitoring the status of devices and systems in real time. They collect data from various sources, including hardware sensors, software logs, and network activity. This data is then analyzed and presented in a user-friendly dashboard, allowing IT teams to quickly identify potential issues and take corrective actions.
For example, an RMM tool can monitor CPU usage, memory utilization, disk space, and network bandwidth on individual computers. If any of these metrics exceed predefined thresholds, the tool can trigger alerts and notifications, alerting IT staff to potential problems. This proactive approach helps prevent performance degradation and downtime.
Generating Reports and Analyzing Data for Insights
RMM tools offer powerful reporting capabilities that enable IT teams to generate detailed reports on various aspects of their IT infrastructure. These reports can include information on device inventory, software usage, security vulnerabilities, and network performance.
The data collected by RMM tools can be analyzed to identify trends and patterns, providing valuable insights into the health and performance of the IT environment. For example, by analyzing historical data on CPU usage, IT teams can identify periods of high resource utilization and optimize system configurations to prevent performance bottlenecks.
The Role of Alerts and Notifications in Proactive Problem Resolution, Rmm remote monitoring and management
Alerts and notifications are crucial components of RMM solutions, enabling proactive problem resolution. RMM tools can be configured to trigger alerts and notifications when certain events occur, such as system failures, security breaches, or performance issues.
These alerts can be delivered via email, SMS, or other communication channels, ensuring that IT staff are promptly notified of any problems. This allows them to take immediate action to resolve issues before they escalate and impact users.
Security Considerations with RMM
Remote monitoring and management (RMM) solutions are powerful tools for managing and securing IT infrastructure. However, with their extensive access to sensitive data and systems, it’s crucial to implement robust security measures to protect against potential threats.
Security Measures for RMM Solutions
RMM solutions provide a central point of control for managing and monitoring devices, making them a prime target for attackers. Implementing appropriate security measures is paramount to ensuring the integrity and confidentiality of data and systems.
- Strong Passwords and Multi-Factor Authentication (MFA): Implement strong password policies for all user accounts and enforce MFA for access to the RMM platform. This adds an extra layer of security by requiring users to provide multiple forms of authentication, making it more difficult for unauthorized individuals to gain access.
- Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and remediate potential weaknesses in the RMM platform and the underlying infrastructure. This proactive approach helps in identifying and addressing vulnerabilities before they can be exploited by attackers.
- Access Control and Role-Based Permissions: Implement granular access control and role-based permissions to limit user access to specific functionalities and data based on their roles and responsibilities. This ensures that only authorized personnel have access to sensitive information and prevents unauthorized modifications or data breaches.
- Encryption in Transit and at Rest: Encrypt all data transmitted between the RMM platform and managed devices using industry-standard protocols such as TLS/SSL. Additionally, encrypt data stored on the RMM platform at rest to protect against unauthorized access even if the platform’s security is compromised.
- Regular Software Updates and Patches: Keep the RMM platform and all managed devices updated with the latest software updates and security patches to mitigate known vulnerabilities and prevent attackers from exploiting outdated software versions.
- Network Segmentation: Segment the RMM platform and managed devices from other networks to limit the potential impact of a security breach. This creates a separate security perimeter, preventing attackers from gaining access to other critical systems.
- Security Monitoring and Logging: Implement comprehensive security monitoring and logging to track user activity, detect suspicious behavior, and identify potential security threats. This provides valuable insights into potential breaches and enables timely responses to security incidents.
RMM’s Contribution to a Robust Security Posture
RMM solutions can significantly contribute to a robust security posture by providing centralized visibility and control over the IT infrastructure. This enables organizations to:
- Proactively Identify and Respond to Security Threats: RMM solutions can monitor systems for suspicious activity, detect malware infections, and alert administrators to potential security breaches. This proactive approach allows for swift response and mitigation of threats before they can cause significant damage.
- Enforce Security Policies and Standards: RMM solutions can be used to enforce security policies and standards across all managed devices, ensuring consistent security practices throughout the organization. This includes implementing strong passwords, disabling unnecessary services, and keeping software up to date.
- Centralize Security Management: RMM solutions provide a centralized platform for managing security tasks, such as patching, vulnerability scanning, and incident response. This simplifies security management, reduces administrative overhead, and ensures consistent security practices across the organization.
- Improve Incident Response: RMM solutions can automate incident response processes, such as isolating infected devices, restoring backups, and notifying relevant personnel. This streamlines incident response, reduces downtime, and minimizes the impact of security breaches.
Mitigating Security Risks Associated with RMM
While RMM solutions offer numerous benefits, it’s important to be aware of the potential security risks and implement appropriate mitigation strategies.
- Data Security and Privacy: RMM solutions handle sensitive data, such as user credentials, system logs, and network traffic. Organizations must ensure that this data is protected with appropriate security measures, including encryption, access control, and data retention policies. Implementing robust data security practices is crucial to comply with data privacy regulations, such as GDPR and CCPA.
- RMM Platform Security: The RMM platform itself needs to be secure to protect against unauthorized access and data breaches. Organizations should choose RMM solutions with a proven track record of security, implement strong authentication mechanisms, and regularly update the platform with security patches.
- Third-Party Integrations: RMM solutions often integrate with third-party applications and services. It’s crucial to carefully vet these integrations and ensure that they meet the organization’s security standards. Organizations should consider the security posture of third-party vendors and implement appropriate security controls for data shared with these integrations.
- User Training and Awareness: User training and awareness are essential for mitigating security risks associated with RMM. Employees should be educated about security best practices, potential threats, and the importance of reporting suspicious activity. This helps to reduce the risk of phishing attacks, malware infections, and other security incidents.
RMM Trends and Future Outlook
The RMM market is continuously evolving, driven by technological advancements and changing IT management needs. This section delves into emerging trends shaping the RMM landscape and explores the impact of technologies like AI and automation. It also provides insights into the future of RMM and its role in the evolving IT management landscape.
Impact of AI and Automation on RMM Solutions
The integration of AI and automation is revolutionizing RMM solutions, enhancing efficiency, accuracy, and proactive problem resolution.
- Automated Patch Management: AI-powered RMM tools can automatically identify and apply software updates across devices, reducing vulnerability risks and improving security posture. For instance, tools can prioritize critical updates, minimizing downtime and ensuring seamless operations.
- Predictive Maintenance: AI algorithms can analyze system data to identify potential issues before they escalate, enabling proactive maintenance and reducing downtime. By predicting hardware failures, organizations can schedule maintenance proactively, minimizing disruptions to critical systems.
- Automated Incident Response: AI-driven RMM solutions can automate incident response processes, reducing the time and effort required to resolve issues. By identifying and prioritizing incidents, these tools can initiate automated remediation actions, minimizing service disruptions.
Predictions about the Future of RMM
The future of RMM is characterized by increased automation, integration with cloud technologies, and a focus on security.
- Increased Automation: RMM solutions will continue to leverage AI and automation to streamline tasks, enhance efficiency, and reduce manual intervention. This will free up IT professionals to focus on more strategic initiatives.
- Cloud Integration: RMM solutions will seamlessly integrate with cloud platforms, enabling centralized management of hybrid IT environments. This integration will provide a unified view of on-premises and cloud-based systems, simplifying management and enhancing security.
- Enhanced Security: RMM solutions will play a crucial role in bolstering security posture. They will integrate with threat intelligence feeds, provide advanced endpoint security features, and automate incident response processes, minimizing the risk of cyberattacks.
Conclusive Thoughts: Rmm Remote Monitoring And Management
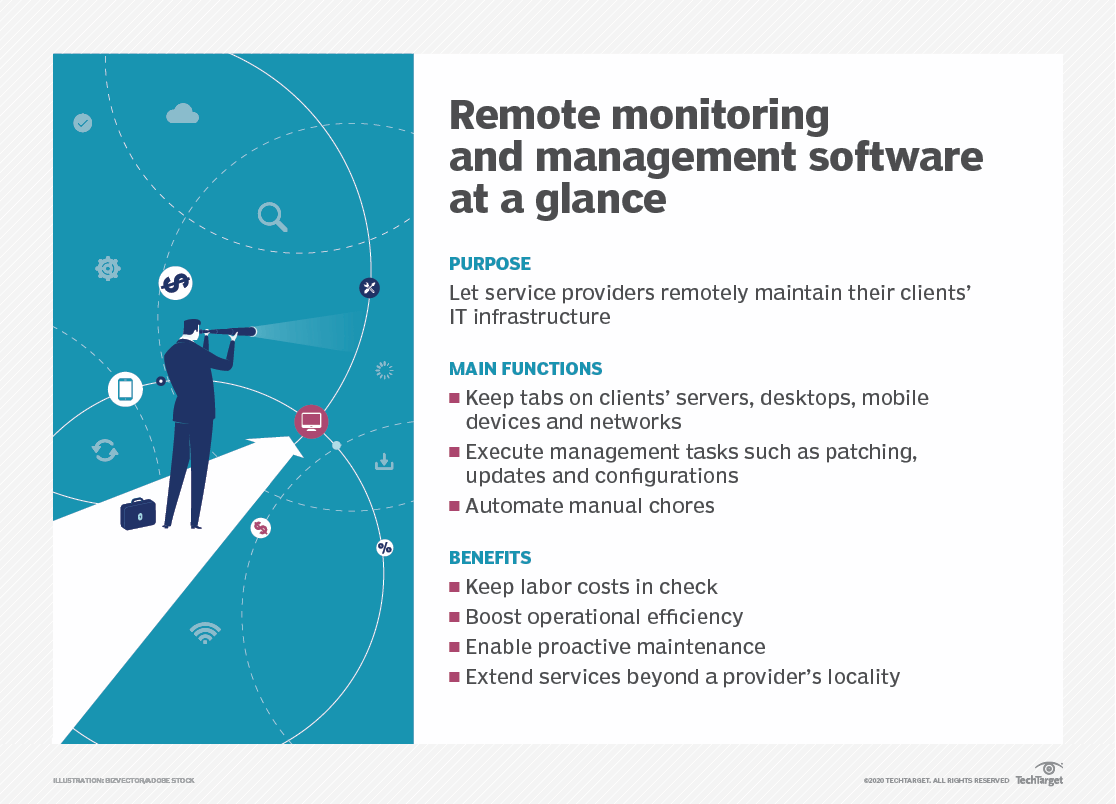
By embracing RMM, businesses can streamline their IT operations, improve efficiency, enhance security, and achieve significant cost savings. With the right RMM solution, organizations can empower their IT teams, foster a proactive approach to IT management, and ultimately, drive business success.
RMM, or remote monitoring and management, helps businesses streamline their IT operations by providing centralized control over devices and systems. When working with RMM, you might need to convert documents to PDF for easier sharing and collaboration, and a small PDF converter can be a valuable tool for this.
With a reliable RMM solution and efficient document conversion, you can ensure your IT infrastructure runs smoothly and securely.