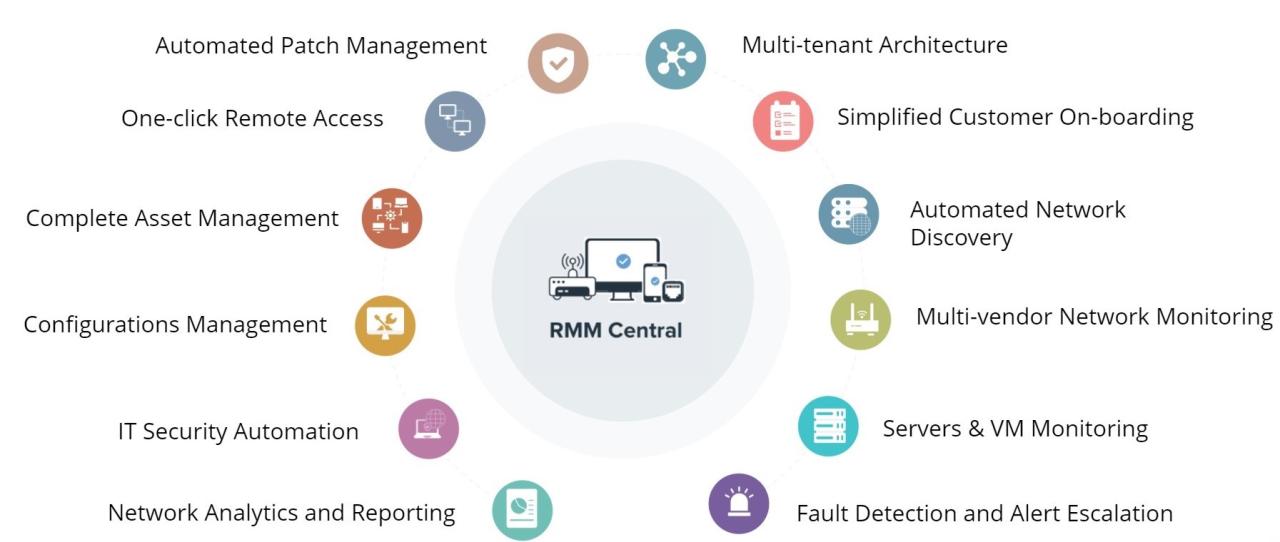
IT RMM, or IT Remote Monitoring and Management, revolutionizes how organizations manage their IT infrastructure. It offers a comprehensive approach that combines proactive monitoring, automated tasks, and remote access, empowering IT teams to work efficiently and effectively.
Table of Contents
ITRMM provides a centralized platform for managing various aspects of IT, including hardware, software, network devices, and security. This allows IT professionals to identify potential issues before they escalate, reducing downtime and improving overall system stability.
ITRMM Overview
ITRMM stands for “Integrated Tax and Revenue Management Model”. It is a comprehensive framework designed to optimize tax and revenue administration, aiming to enhance efficiency, transparency, and accountability in public financial management.
ITRMM Definition
ITRMM is a holistic approach to tax and revenue management that encompasses all aspects of the revenue cycle, from policy formulation to collection and enforcement. It seeks to create a seamless and integrated system that leverages technology and data analytics to improve revenue performance.
ITRMM Principles
The key principles behind ITRMM include:
- Transparency and Accountability: ITRMM emphasizes open and transparent processes, ensuring that taxpayers understand their obligations and that revenue collection is conducted fairly and ethically.
- Efficiency and Effectiveness: The model aims to streamline processes, reduce administrative burdens, and improve the overall efficiency of tax and revenue administration.
- Data-Driven Decision Making: ITRMM leverages data analytics to gain insights into taxpayer behavior, identify potential revenue leakage, and inform policy decisions.
- Technology Integration: The model promotes the use of technology to automate processes, improve data management, and enhance communication with taxpayers.
- Stakeholder Engagement: ITRMM recognizes the importance of engaging with taxpayers, businesses, and other stakeholders to ensure their needs are considered and to foster trust and collaboration.
ITRMM History and Evolution
The concept of ITRMM emerged in the early 2000s as a response to the need for more effective and efficient tax and revenue administration. It has evolved over time, incorporating best practices and lessons learned from various countries and organizations.
Benefits of ITRMM
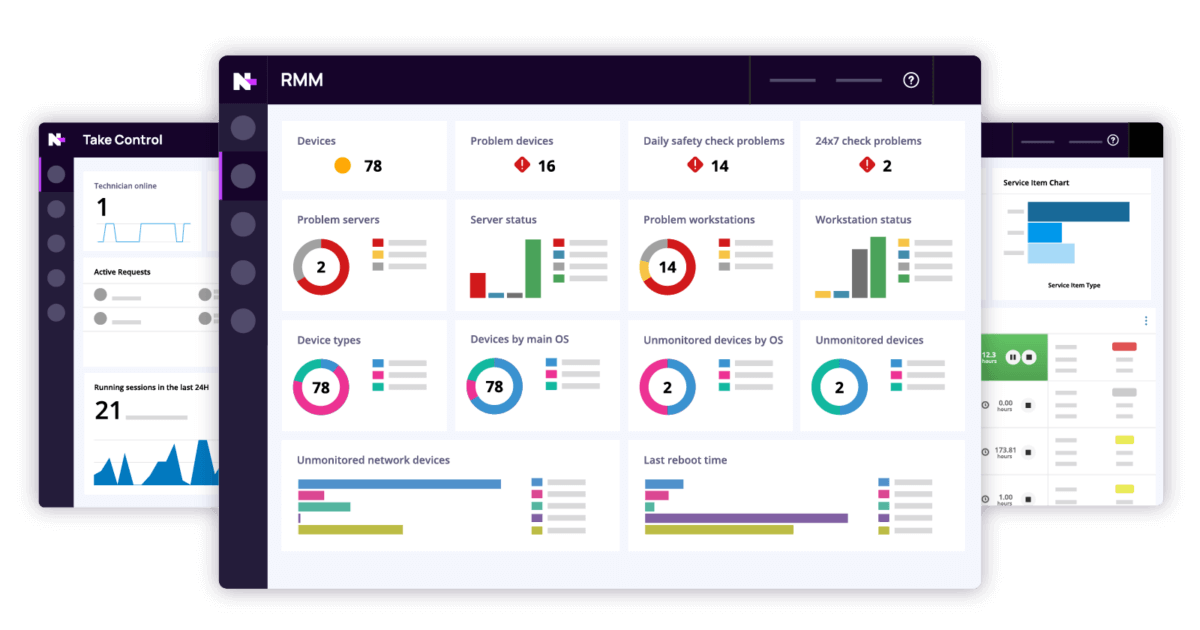
ITRMM (Integrated IT Risk Management and Monitoring) offers a comprehensive approach to managing IT risks, providing significant advantages over traditional methods. This approach goes beyond simply identifying and mitigating risks; it encompasses a holistic view of IT security, incorporating continuous monitoring and proactive risk management.
Improved Risk Management
ITRMM enhances risk management by integrating various aspects of IT security into a single framework. This framework provides a comprehensive view of potential risks, allowing organizations to identify, assess, and prioritize them effectively.
- Comprehensive Risk Assessment: ITRMM facilitates a more comprehensive risk assessment by considering all potential threats and vulnerabilities across the entire IT infrastructure. This approach helps identify risks that may be overlooked in traditional methods, which often focus on specific security aspects.
- Proactive Risk Mitigation: ITRMM encourages proactive risk mitigation by enabling organizations to implement preventative measures before vulnerabilities are exploited. This approach reduces the likelihood of security breaches and minimizes the impact of potential incidents.
- Continuous Monitoring: ITRMM emphasizes continuous monitoring of IT systems and processes to detect and respond to emerging threats in real time. This allows organizations to identify potential risks early on and take swift action to mitigate them before they escalate.
Enhanced Operational Efficiency
ITRMM streamlines IT operations by automating tasks and integrating security measures into existing workflows. This approach improves operational efficiency and reduces the likelihood of human error, ultimately enhancing the overall security posture of the organization.
- Automated Tasks: ITRMM automates routine security tasks such as vulnerability scanning, patch management, and incident response, freeing up IT staff to focus on more strategic initiatives. This approach improves operational efficiency and reduces the workload on IT teams.
- Streamlined Processes: ITRMM integrates security measures into existing workflows, simplifying security processes and making them more efficient. This approach reduces the complexity of managing IT security and improves overall operational efficiency.
- Reduced Costs: ITRMM can lead to significant cost savings by reducing the number of security incidents and minimizing the impact of those that do occur. This approach also reduces the need for costly security audits and remediation efforts.
Improved Compliance
ITRMM helps organizations comply with industry regulations and legal requirements by providing a framework for managing IT risks and ensuring compliance with relevant standards. This approach simplifies compliance efforts and reduces the risk of penalties and fines.
- Centralized Compliance Management: ITRMM provides a centralized platform for managing compliance requirements, streamlining the process and making it easier to track progress and demonstrate compliance.
- Automated Reporting: ITRMM automates the generation of compliance reports, reducing the time and effort required to document compliance efforts. This approach simplifies compliance reporting and reduces the risk of errors.
- Improved Audit Readiness: ITRMM helps organizations prepare for audits by providing a comprehensive view of their security posture and compliance status. This approach reduces the risk of audit findings and facilitates a smoother audit process.
Enhanced Business Continuity
ITRMM strengthens business continuity by minimizing the impact of security incidents and ensuring the availability of critical IT systems and data. This approach helps organizations recover quickly from disruptions and minimize business downtime.
- Disaster Recovery Planning: ITRMM facilitates effective disaster recovery planning by identifying critical systems and data and developing strategies to ensure their availability in the event of a disaster. This approach helps organizations recover quickly from disruptions and minimize business downtime.
- Business Impact Analysis: ITRMM supports business impact analysis by identifying the potential impact of security incidents on business operations. This approach helps organizations prioritize security measures and allocate resources effectively.
- Incident Response: ITRMM streamlines incident response by providing a framework for managing security incidents and ensuring timely and effective responses. This approach minimizes the impact of security incidents and reduces the risk of data breaches.
Increased Business Agility
ITRMM empowers organizations to adapt to changing business needs and market conditions by providing a flexible and scalable approach to managing IT risks. This approach helps organizations respond quickly to new threats and opportunities and maintain a competitive edge.
- Scalability: ITRMM can be scaled to meet the evolving needs of organizations, providing a flexible approach to managing IT risks as the organization grows and changes.
- Adaptability: ITRMM allows organizations to adapt to changing security threats and industry regulations by providing a framework for continuous improvement and risk assessment.
- Innovation: ITRMM supports innovation by providing a secure foundation for organizations to experiment with new technologies and business models. This approach helps organizations stay ahead of the curve and maintain a competitive edge.
Table: Key Benefits of ITRMM
| Benefit | Description |
|—|—|
| Improved Risk Management | Comprehensive risk assessment, proactive mitigation, continuous monitoring |
| Enhanced Operational Efficiency | Automated tasks, streamlined processes, reduced costs |
| Improved Compliance | Centralized compliance management, automated reporting, improved audit readiness |
| Enhanced Business Continuity | Disaster recovery planning, business impact analysis, incident response |
| Increased Business Agility | Scalability, adaptability, innovation |
ITRMM Implementation
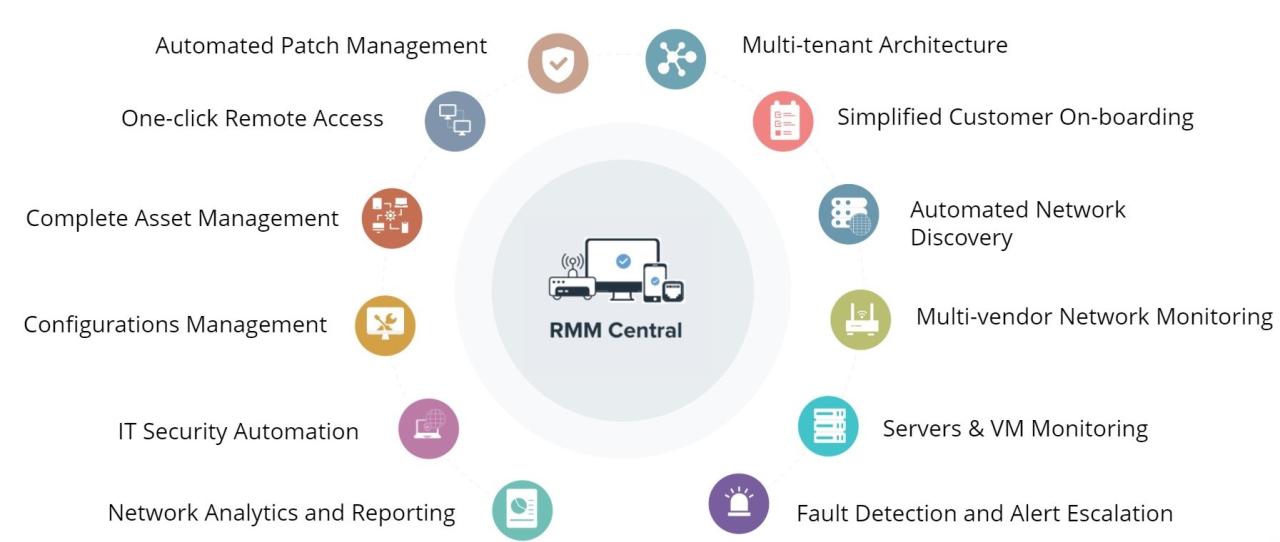
Implementing ITRMM effectively requires a structured approach that considers the unique needs of your organization. A well-defined plan can ensure a smooth transition and maximize the benefits of this technology.
Steps Involved in ITRMM Implementation
The implementation process for ITRMM involves a series of steps that are essential for successful integration.
- Needs Assessment: Begin by understanding your organization’s specific requirements and challenges. This involves identifying the key areas where ITRMM can provide value, such as improving data accuracy, streamlining processes, or enhancing security.
- Solution Design: Based on the needs assessment, design a tailored ITRMM solution that aligns with your existing IT infrastructure and business processes. This may involve selecting appropriate tools and technologies, defining data mapping strategies, and establishing integration points.
- Pilot Implementation: Conduct a pilot implementation to test the ITRMM solution in a controlled environment. This allows you to identify and address potential issues before full-scale deployment.
- Full Deployment: Once the pilot is successful, roll out the ITRMM solution across your organization. This involves training users, migrating data, and ensuring smooth integration with existing systems.
- Monitoring and Optimization: Continuously monitor the performance of the ITRMM solution and make necessary adjustments to optimize its effectiveness. This includes tracking key metrics, analyzing data, and identifying areas for improvement.
Step-by-Step Guide for Successful ITRMM Implementation
A structured approach to implementing ITRMM can significantly increase the chances of success.
- Define Clear Objectives: Begin by establishing clear and measurable objectives for your ITRMM implementation. What are you hoping to achieve? Improved data quality? Reduced processing time? Enhanced security? Clearly defined objectives will guide your implementation process and ensure that you are on track to achieve your goals.
- Identify Stakeholders: Engage all relevant stakeholders in the implementation process. This includes IT professionals, business users, and management. Early involvement will foster collaboration and ensure that everyone is aligned on the goals and benefits of ITRMM.
- Develop a Detailed Plan: Create a comprehensive implementation plan that Artikels the steps involved, timelines, resources required, and key milestones. A detailed plan will provide a roadmap for your implementation and help you stay organized and on schedule.
- Choose the Right Tools and Technologies: Select tools and technologies that are compatible with your existing IT infrastructure and meet your specific requirements. Consider factors such as data volume, complexity, and security needs. A well-chosen technology stack will lay the foundation for a robust and scalable ITRMM solution.
- Implement in Phases: Implementing ITRMM in phases allows you to test and refine the solution incrementally, minimizing the risk of disruptions and maximizing the chances of success. Start with a pilot project, then gradually expand the implementation across your organization.
- Provide Training and Support: Ensure that all users are adequately trained on how to use the ITRMM solution. Provide ongoing support and documentation to address any questions or issues that may arise. Effective training and support will empower users to leverage the full potential of ITRMM.
- Monitor and Evaluate: Regularly monitor the performance of your ITRMM solution and collect feedback from users. This will help you identify areas for improvement and ensure that the solution continues to meet your evolving needs. Continuous monitoring and evaluation are essential for optimizing the effectiveness of ITRMM.
Best Practices for Integrating ITRMM into Existing IT Systems
Integrating ITRMM into existing IT systems requires careful planning and execution.
- Assess Compatibility: Before implementing ITRMM, carefully assess the compatibility of your existing IT systems with the chosen tools and technologies. Ensure that the integration process will be smooth and minimize disruptions to your operations.
- Establish Clear Integration Points: Define clear integration points between ITRMM and your existing systems. This involves mapping data fields, establishing communication protocols, and defining data exchange mechanisms. Well-defined integration points will ensure seamless data flow and prevent errors.
- Implement Data Validation: Implement data validation procedures to ensure that the data being integrated into ITRMM is accurate and consistent. This involves setting up data quality checks and validation rules. Data validation is crucial for maintaining the integrity and reliability of your ITRMM solution.
- Test Thoroughly: Conduct thorough testing to ensure that the integration process is working as expected. This involves simulating real-world scenarios and testing different data flows. Thorough testing will help you identify and address any issues before full-scale deployment.
- Document the Integration Process: Document the entire integration process, including the steps involved, data mapping, and any configuration settings. Detailed documentation will facilitate future maintenance, troubleshooting, and updates.
Challenges and Considerations During ITRMM Implementation
Implementing ITRMM can present various challenges.
- Data Complexity: Organizations often deal with complex and heterogeneous data sets. Integrating this data into ITRMM can be challenging, requiring careful data mapping, cleansing, and transformation. Data complexity requires a robust data management strategy and appropriate tools to ensure accurate and reliable data integration.
- Integration with Existing Systems: Integrating ITRMM with existing IT systems can be complex and require significant effort. This involves ensuring compatibility, establishing communication protocols, and handling data flow between systems. Careful planning, thorough testing, and skilled technical resources are essential for successful integration.
- User Adoption: Encouraging user adoption of ITRMM is crucial for its success. Users may resist change or find it difficult to adapt to new workflows. Effective training, communication, and support are essential to overcome user resistance and promote widespread adoption.
- Security and Privacy: ITRMM often involves handling sensitive data, making security and privacy a top priority. Organizations need to implement robust security measures to protect data from unauthorized access, modification, or disclosure. Compliance with relevant data privacy regulations is also essential.
- Cost and Resources: Implementing ITRMM can require significant investment in terms of time, resources, and expertise. Organizations need to carefully assess the costs and benefits of ITRMM and ensure that they have the necessary resources to support the implementation process. A well-defined budget and resource allocation plan are essential for successful implementation.
ITRMM Tools and Technologies
ITRMM relies on a suite of tools and technologies to effectively manage risks, identify opportunities, and optimize business processes. These tools facilitate data collection, analysis, and communication, enabling organizations to make informed decisions and improve their overall performance.
ITRMM Tool Comparison
A range of ITRMM tools is available, each with its own unique features and capabilities. The choice of tool depends on the specific needs and requirements of the organization. Here is a comparison of some popular ITRMM tools:
- Risk Management Software: These platforms provide comprehensive risk management capabilities, including risk identification, assessment, mitigation planning, and monitoring. Features typically include risk registers, dashboards, reporting tools, and integration with other enterprise systems.
- Data Analytics Tools: Data analytics tools are crucial for ITRMM as they help analyze vast amounts of data to identify patterns, trends, and potential risks. These tools can be used to perform statistical analysis, predictive modeling, and risk scoring.
- Collaboration Platforms: Collaboration platforms enable effective communication and information sharing among stakeholders involved in ITRMM. These platforms provide features such as document sharing, task management, and real-time communication channels.
Popular ITRMM Platforms
Several popular ITRMM platforms offer a range of functionalities to support organizations in their risk management efforts. These platforms typically provide a combination of risk management, data analytics, and collaboration tools:
- Riskonnect: This platform offers a comprehensive suite of risk management tools, including risk assessment, mitigation planning, and reporting. It also integrates with other enterprise systems, enabling seamless data flow.
- LogicManager: LogicManager provides a cloud-based risk management platform that caters to various industries. Its features include risk identification, assessment, mitigation planning, and reporting. It also offers data analytics capabilities for risk insights.
- Protiviti Risk & Compliance: Protiviti offers a range of risk management solutions, including its Risk & Compliance platform. This platform provides comprehensive risk management capabilities, including risk assessment, mitigation planning, and reporting. It also offers data analytics and collaboration tools.
Key ITRMM Tools and Capabilities
The following table Artikels some key ITRMM tools and their capabilities:
| Tool | Capabilities |
|---|---|
| Risk Management Software | Risk identification, assessment, mitigation planning, monitoring, reporting, integration with other systems |
| Data Analytics Tools | Statistical analysis, predictive modeling, risk scoring, data visualization, trend analysis |
| Collaboration Platforms | Document sharing, task management, real-time communication, information sharing, stakeholder engagement |
| Business Intelligence Tools | Data visualization, reporting, dashboards, performance monitoring, trend analysis |
| Compliance Management Software | Compliance monitoring, policy management, audit scheduling, reporting, risk assessment |
ITRMM Trends and Future Directions
The field of ITRMM is constantly evolving, driven by advancements in technology and the ever-changing needs of IT organizations. Understanding these trends is crucial for organizations seeking to optimize their IT operations and stay ahead of the curve. This section delves into emerging trends, future innovations, and the potential impact of these advancements on the future of ITRMM.
Emerging Trends in ITRMM, It rmm
Emerging trends in ITRMM are shaping the way IT organizations manage their resources and deliver services. These trends are driven by factors such as the increasing adoption of cloud computing, the rise of automation, and the growing importance of data analytics.
- Cloud-Native ITRMM: The shift towards cloud computing has significantly impacted ITRMM. Organizations are increasingly adopting cloud-native solutions, which are designed to run seamlessly in cloud environments. This trend is leading to the development of new ITRMM tools and methodologies specifically tailored for cloud-based infrastructure. For example, cloud monitoring tools provide real-time insights into the performance and health of cloud applications, while cloud cost optimization tools help organizations manage their cloud expenses efficiently.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are transforming various aspects of ITRMM, including incident management, capacity planning, and performance optimization. AI-powered systems can analyze vast amounts of data to identify patterns, predict potential issues, and automate routine tasks. For instance, AI-driven incident management systems can automatically categorize incidents, assign them to the appropriate teams, and even suggest possible solutions. ML algorithms can analyze historical data to predict future resource requirements, enabling proactive capacity planning and reducing the risk of performance bottlenecks.
- DevOps and Agile ITRMM: DevOps and Agile methodologies are becoming increasingly popular in IT organizations, promoting collaboration between development and operations teams. ITRMM is adapting to these methodologies by embracing automation, continuous monitoring, and a focus on delivering value quickly and efficiently. Tools and practices that support continuous integration and continuous delivery (CI/CD) are becoming essential components of ITRMM, enabling organizations to deploy software updates and changes more frequently and with greater reliability.
- Data-Driven ITRMM: Data analytics is playing a crucial role in ITRMM, enabling organizations to gain deeper insights into their IT operations. By analyzing data from various sources, such as monitoring tools, logs, and user feedback, organizations can identify trends, diagnose problems, and optimize performance. Data-driven insights can also be used to make informed decisions about IT investments and resource allocation.
Future Advancements and Innovations in ITRMM Technologies
The future of ITRMM holds exciting possibilities, driven by continuous innovation in technology. Organizations can expect to see advancements in areas such as:
- Predictive Analytics and AI-Powered Automation: Predictive analytics will play a more prominent role in ITRMM, enabling organizations to anticipate and prevent issues before they occur. AI-powered automation will further enhance efficiency, automating routine tasks and freeing up IT teams to focus on more strategic initiatives. For example, AI-driven systems can analyze data from multiple sources to predict potential outages or performance bottlenecks, allowing IT teams to proactively address these issues before they impact users.
- Integration with Emerging Technologies: ITRMM tools and technologies will integrate with emerging technologies such as blockchain, edge computing, and the Internet of Things (IoT). Blockchain can enhance security and transparency in IT operations, while edge computing can improve performance and reduce latency for applications deployed at the edge of the network. The growing number of connected devices and sensors in the IoT will require new ITRMM approaches to manage and monitor these devices effectively.
- Enhanced User Experience and Collaboration: ITRMM tools will become more user-friendly, providing intuitive interfaces and real-time insights. Collaboration features will be enhanced, enabling IT teams to work together more effectively and share information seamlessly. For example, ITRMM dashboards will provide a comprehensive view of IT operations, allowing teams to monitor key performance indicators (KPIs) and identify potential issues quickly.
Predictions for the Future of ITRMM and its Impact on IT Management
The future of ITRMM is characterized by increasing automation, intelligent insights, and a focus on delivering value to the business. Here are some predictions for the future of ITRMM:
- Shift from Reactive to Proactive Management: ITRMM will move away from reactive problem-solving towards proactive management. AI-powered tools will enable organizations to predict and prevent issues before they occur, reducing downtime and improving service availability.
- Increased Focus on Business Outcomes: ITRMM will increasingly focus on aligning IT operations with business goals. IT teams will be expected to demonstrate the value they deliver to the business, using data and analytics to measure the impact of their efforts.
- Evolution of IT Roles: The role of IT professionals will evolve as automation and AI take over routine tasks. IT teams will need to develop new skills in areas such as data analytics, AI, and cloud computing to manage and optimize complex IT environments.
Potential Impact of Emerging Technologies on ITRMM
Emerging technologies are poised to significantly impact ITRMM, transforming the way IT organizations manage their resources and deliver services.
- Cloud Computing: The adoption of cloud computing is driving the development of cloud-native ITRMM solutions, enabling organizations to manage their IT resources more efficiently and cost-effectively. Cloud-based monitoring tools provide real-time insights into the performance and health of cloud applications, while cloud cost optimization tools help organizations manage their cloud expenses effectively.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are transforming various aspects of ITRMM, automating routine tasks, providing intelligent insights, and enabling proactive problem-solving. AI-powered systems can analyze vast amounts of data to identify patterns, predict potential issues, and suggest possible solutions.
- Internet of Things (IoT): The growing number of connected devices and sensors in the IoT will require new ITRMM approaches to manage and monitor these devices effectively. ITRMM tools will need to integrate with IoT platforms to provide comprehensive visibility into the performance and health of IoT devices.
- Blockchain: Blockchain technology can enhance security and transparency in IT operations. Blockchain-based systems can track and audit IT assets, ensuring their authenticity and integrity. Blockchain can also be used to manage access control and permissions, enhancing security and reducing the risk of unauthorized access.
- Edge Computing: Edge computing is transforming the way applications are deployed and managed. ITRMM tools will need to adapt to edge computing environments, providing monitoring and management capabilities for applications deployed at the edge of the network.
Case Studies of ITRMM Success: It Rmm
ITRMM implementation has proven successful in various organizations across different industries. These case studies highlight the practical application of ITRMM principles and the tangible benefits realized. They provide valuable insights into the challenges faced, solutions adopted, and the impact on business outcomes.
Case Study 1: Manufacturing Company
This case study focuses on a large manufacturing company that implemented ITRMM to improve its supply chain efficiency and reduce costs.
The company faced several challenges, including:
– Long lead times for raw materials
– Inventory management inefficiencies
– High transportation costs
To address these challenges, the company implemented ITRMM principles, including:
– Real-time inventory tracking
– Demand forecasting and planning
– Optimized transportation routes
The implementation of ITRMM resulted in significant improvements, including:
– Reduced lead times by 20%
– Inventory levels decreased by 15%
– Transportation costs reduced by 10%
Case Study 2: Retail Company
This case study explores the implementation of ITRMM in a large retail company to enhance customer service and improve operational efficiency.
The company faced challenges such as:
– Long wait times at customer service desks
– Inefficient order fulfillment processes
– Lack of real-time visibility into inventory levels
The company implemented ITRMM principles, including:
– Real-time customer service tracking
– Automated order fulfillment systems
– Inventory management optimization
The implementation of ITRMM resulted in:
– Reduced customer wait times by 30%
– Increased order fulfillment efficiency by 25%
– Improved inventory accuracy by 10%
Case Study 3: Healthcare Provider
This case study examines the use of ITRMM in a healthcare provider to enhance patient care and improve operational efficiency.
The healthcare provider faced challenges such as:
– Inefficient patient scheduling systems
– Lack of real-time access to patient records
– High administrative costs
The healthcare provider implemented ITRMM principles, including:
– Real-time patient scheduling
– Electronic health records (EHR) systems
– Automated billing and claims processing
The implementation of ITRMM resulted in:
– Reduced patient wait times by 20%
– Improved patient satisfaction scores by 15%
– Reduced administrative costs by 10%
Conclusive Thoughts
ITRMM is a powerful tool for streamlining IT operations, enhancing security, and boosting efficiency. By embracing its principles and leveraging the right tools and technologies, organizations can unlock the full potential of their IT infrastructure and gain a competitive advantage in today’s digital landscape.
It RMM is a powerful tool for automating repetitive tasks, and when you need to take your automation to the next level, you might want to consider using imacros. This browser extension allows you to record and replay web interactions, making it ideal for tasks like data scraping, form filling, and website testing.
While It RMM focuses on system management, imacros provides a complementary approach for web-based automation, giving you a more comprehensive solution for streamlining your workflows.