Remote monitoring and management rmm software – Remote monitoring and management (RMM) software has become an indispensable tool for businesses of all sizes, enabling them to manage their IT infrastructure remotely and efficiently. RMM solutions provide a centralized platform for monitoring, managing, and securing endpoints, servers, and networks, streamlining IT operations and enhancing productivity.
Table of Contents
By leveraging RMM software, organizations can automate routine tasks, proactively identify and resolve issues, improve security posture, and optimize overall IT performance. From patch management and endpoint security to remote access and reporting, RMM solutions offer a comprehensive suite of features designed to empower IT teams and ensure business continuity.
Introduction to Remote Monitoring and Management (RMM) Software
Remote monitoring and management (RMM) software is a powerful tool that helps businesses of all sizes manage and secure their IT infrastructure remotely. RMM solutions provide a centralized platform for monitoring and managing devices, networks, and applications, offering significant advantages in terms of efficiency, security, and cost savings.
Core Functionalities of RMM Software
RMM software offers a comprehensive set of features designed to simplify IT management and enhance security. Here are some key functionalities:
- Remote Access and Control: RMM solutions enable IT administrators to access and control devices remotely, allowing them to troubleshoot issues, install software, and manage configurations from anywhere with an internet connection.
- Network Monitoring: RMM software continuously monitors network performance, identifying potential bottlenecks, security threats, and other issues that could impact business operations. Real-time monitoring alerts administrators to problems, enabling prompt resolution and minimizing downtime.
- Endpoint Security: RMM solutions provide robust endpoint security features, including antivirus protection, patch management, and vulnerability scanning. This helps protect devices from malware, ransomware, and other cyber threats.
- Software Deployment and Patching: RMM software automates software deployment and patching processes, ensuring all devices have the latest updates and security patches. This helps maintain system stability and minimize security vulnerabilities.
- Asset Management: RMM solutions provide a centralized inventory of all IT assets, including hardware, software, and licenses. This information helps IT teams manage resources effectively and track asset lifecycles.
- Reporting and Analytics: RMM software generates detailed reports on system performance, security events, and other key metrics. These reports provide valuable insights into IT operations and help identify areas for improvement.
Examples of Automated Tasks
RMM software automates many common IT tasks, freeing up IT staff to focus on more strategic initiatives. Here are some examples:
- Automatic Software Updates: RMM solutions can automatically download and install software updates, ensuring all devices are running the latest versions.
- Automated Patch Management: RMM software can automatically identify and apply security patches, reducing the risk of vulnerabilities and attacks.
- Scheduled Backups: RMM solutions can automatically back up data to ensure data integrity and recovery in case of system failures or disasters.
- Remote Device Monitoring: RMM software can continuously monitor the health and performance of devices, alerting administrators to potential issues before they impact users.
- Proactive Security Monitoring: RMM solutions can scan for vulnerabilities and security threats, alerting administrators to potential risks and enabling timely remediation.
Benefits of Implementing RMM
RMM software offers significant benefits for businesses of all sizes. Here are some key advantages:
- Improved Efficiency: RMM solutions automate many routine IT tasks, freeing up IT staff to focus on more strategic initiatives.
- Enhanced Security: RMM software provides comprehensive security features, including antivirus protection, patch management, and vulnerability scanning, to protect against cyber threats.
- Reduced Costs: RMM solutions can help businesses reduce IT costs by automating tasks, minimizing downtime, and preventing security breaches.
- Improved User Experience: RMM solutions ensure devices are running smoothly and efficiently, providing a positive user experience for employees and customers.
- Increased Productivity: RMM software helps businesses maintain a stable and secure IT infrastructure, minimizing downtime and maximizing productivity.
- Scalability: RMM solutions can easily scale to accommodate the growth of businesses, providing a flexible and cost-effective way to manage IT infrastructure.
Key Features of RMM Software
RMM software offers a suite of features designed to streamline IT management tasks and improve overall system health. These features empower IT professionals to proactively manage endpoints, automate routine tasks, and ensure business continuity.
Remote Access
Remote access is a cornerstone of RMM software, allowing IT professionals to connect to and manage endpoints remotely. This feature eliminates the need for physical presence at the device, significantly reducing downtime and travel costs.
- Secure Connection: RMM software uses secure protocols like SSH and HTTPS to establish encrypted connections, safeguarding sensitive data during remote sessions.
- Remote Control: IT professionals can take full control of remote devices, enabling them to troubleshoot issues, install software, and perform other tasks as if they were physically present.
- File Transfer: RMM software facilitates the transfer of files between the technician’s workstation and the remote device, simplifying software updates, data backups, and other file management tasks.
Patch Management
Patch management is a critical aspect of endpoint security, ensuring that devices are protected against vulnerabilities and malware. RMM software automates this process, streamlining patch deployment and reducing the risk of security breaches.
- Automated Patching: RMM software automatically identifies missing patches and deploys them to endpoints without manual intervention, ensuring that devices are always up-to-date.
- Patch Scheduling: IT professionals can schedule patch deployments to minimize disruptions to users, allowing them to install patches during off-peak hours or when devices are not in use.
- Vulnerability Assessment: RMM software scans endpoints for known vulnerabilities, identifying potential security risks and providing actionable insights to mitigate them.
Endpoint Security
Endpoint security is paramount in today’s threat landscape. RMM software provides a comprehensive suite of features to protect endpoints from malware, ransomware, and other cyber threats.
- Antivirus and Anti-Malware: RMM software integrates with leading antivirus and anti-malware solutions, providing real-time protection against known and emerging threats.
- Firewall Management: RMM software allows IT professionals to configure and manage firewalls on endpoints, restricting access to potentially harmful networks and applications.
- Data Loss Prevention: RMM software can enforce data loss prevention policies, preventing sensitive information from being transmitted to unauthorized recipients.
Reporting
RMM software generates detailed reports that provide valuable insights into the health and performance of IT infrastructure. These reports help IT professionals identify trends, troubleshoot issues, and make informed decisions about resource allocation.
- System Health Reports: RMM software provides comprehensive reports on the health and performance of endpoints, including hardware utilization, software updates, and security status.
- Performance Monitoring Reports: These reports track key performance indicators (KPIs) such as network bandwidth usage, CPU utilization, and disk space availability, providing insights into system performance and potential bottlenecks.
- Security Event Logs: RMM software captures security events, such as failed login attempts, malware detections, and unauthorized software installations, enabling IT professionals to identify and respond to security threats.
Deployment and Integration of RMM Software
Deploying and integrating RMM software within your IT infrastructure can significantly improve your ability to manage and secure your network. This section explores the best practices for deployment, considerations for choosing the right RMM solution, and a step-by-step guide for configuration and customization.
Best Practices for Deployment and Integration
Deploying RMM software effectively requires careful planning and execution. The following best practices can help ensure a smooth and successful integration:
- Start with a Pilot Deployment: Begin with a pilot deployment on a small group of devices to test the software’s functionality and identify any potential issues. This allows for adjustments and refinements before a full-scale rollout.
- Thorough Documentation: Maintain detailed documentation of the deployment process, including configurations, policies, and any encountered challenges. This documentation will be invaluable for troubleshooting and future updates.
- Effective Communication: Keep your team informed about the RMM deployment process, its benefits, and any potential changes in workflows. Clear communication minimizes resistance and promotes user adoption.
- Regular Monitoring and Updates: Continuously monitor the RMM platform’s performance, update the software regularly, and ensure that all devices are properly managed. This proactive approach helps prevent potential problems and maximizes the software’s benefits.
Choosing the Right RMM Solution
Selecting the appropriate RMM solution is crucial for maximizing its benefits and meeting your organization’s specific needs. Consider the following factors when making your decision:
- Organizational Needs: Identify the specific needs and challenges your organization faces in managing and securing its IT infrastructure. This will guide your choice of features and functionalities.
- Budget Constraints: RMM solutions vary significantly in price. Establish a clear budget and prioritize features that align with your financial constraints.
- Scalability and Flexibility: Choose a solution that can scale with your organization’s growth and adapt to evolving IT needs. Look for features like multi-tenant support and customizable dashboards.
- Integration Capabilities: Consider the solution’s ability to integrate with your existing IT infrastructure, such as Active Directory, help desk systems, and other tools. Seamless integration minimizes complexity and improves efficiency.
- Customer Support: Evaluate the vendor’s reputation for customer support and technical assistance. Choose a solution with responsive and knowledgeable support to address any issues promptly.
Configuring and Customizing an RMM Platform
Once you’ve chosen an RMM solution, the next step is to configure and customize it to meet your organization’s specific requirements. This involves:
- Defining User Roles and Permissions: Establish different user roles with appropriate access levels to the RMM platform. This ensures security and prevents unauthorized access to sensitive information.
- Setting Up Monitoring Policies: Configure monitoring policies for various aspects of your IT infrastructure, including system performance, security events, and software updates. These policies define the triggers for alerts and notifications.
- Creating Patch Management Rules: Implement patch management rules to automate the process of installing software updates and security patches on managed devices. This helps maintain system security and stability.
- Configuring Alert and Notification Systems: Set up alert and notification systems to inform the appropriate personnel of critical events, such as system failures, security breaches, or software update failures.
- Customizing Dashboards and Reports: Design customized dashboards and reports to visualize key performance indicators (KPIs) and track the health and security of your IT infrastructure.
RMM Software in Action
RMM software isn’t just a theoretical concept; it’s a powerful tool that’s actively used in a wide range of industries to manage and secure IT infrastructure. Let’s explore some real-world examples of how RMM solutions are deployed and the benefits they deliver.
RMM in Healthcare
Healthcare organizations face unique IT challenges, such as HIPAA compliance, patient data security, and the need for reliable access to critical systems. RMM software plays a crucial role in addressing these challenges:
- HIPAA Compliance: RMM tools help healthcare providers enforce security policies, monitor system activity, and track changes, ensuring compliance with HIPAA regulations.
- Patient Data Security: RMM solutions provide real-time monitoring of endpoints, detecting and responding to potential security threats that could compromise patient data.
- Remote Access and Support: RMM software enables healthcare professionals to remotely access and manage patient records, medical devices, and other critical systems, improving efficiency and patient care.
RMM in Education
Educational institutions are increasingly reliant on technology, but managing a diverse IT environment can be a complex task. RMM software provides essential support for schools and universities:
- Software Deployment and Updates: RMM tools streamline the process of deploying and updating software across multiple devices, ensuring students and faculty have access to the latest applications and security patches.
- Device Management: RMM solutions allow administrators to remotely manage and monitor student and faculty devices, ensuring proper configuration and performance.
- Troubleshooting and Support: RMM software provides remote access and support capabilities, allowing IT staff to quickly resolve technical issues and minimize disruptions to learning.
RMM in Finance
The financial services industry is highly regulated and faces constant threats from cyberattacks. RMM software plays a vital role in protecting sensitive financial data:
- Security Monitoring and Threat Detection: RMM tools provide real-time monitoring of network activity, identifying suspicious behavior and potential security breaches.
- Vulnerability Management: RMM solutions help financial institutions identify and patch vulnerabilities in their systems, reducing the risk of exploitation by malicious actors.
- Compliance and Audit: RMM software helps organizations track and document security configurations, simplifying compliance audits and demonstrating adherence to industry regulations.
RMM Use Cases and Benefits
The following table summarizes some common RMM use cases, the specific challenges addressed, and the resulting benefits:
| Use Case | Challenge | Benefit |
|---|---|---|
| Endpoint Security | Protecting devices from malware and cyberattacks | Reduced risk of data breaches and system downtime |
| Software Patching | Ensuring systems are up-to-date with security patches | Improved security posture and reduced vulnerability to exploits |
| Remote Access and Support | Providing timely IT support to users in remote locations | Increased productivity and reduced downtime |
| Asset Management | Tracking and managing hardware and software assets | Improved inventory control and cost optimization |
| Performance Monitoring | Identifying and resolving performance issues in systems and applications | Improved system stability and user experience |
Cost and Return on Investment (ROI)
RMM software, while offering significant benefits, also involves costs that need careful consideration. Evaluating the cost factors and potential return on investment (ROI) is crucial for making an informed decision.
The cost of implementing and maintaining RMM software varies depending on factors such as the size of your organization, the features you require, and the specific vendor you choose.
Cost Factors
The cost of RMM software can be broken down into several key factors:
- Software Licensing: This is the primary cost associated with RMM software. Pricing models vary, with some vendors offering per-device pricing while others use a subscription-based model. The cost of licensing will depend on the number of devices you need to manage and the features included in the plan.
- Implementation and Setup: Implementing RMM software may require professional services to configure and integrate it with your existing IT infrastructure. The cost of implementation can vary based on the complexity of your environment and the level of support you require.
- Ongoing Maintenance: RMM software requires regular updates and maintenance to ensure optimal performance and security. This may involve additional costs for software updates, technical support, and training for your IT team.
- Hardware Costs: Depending on your chosen RMM solution, you may need to invest in additional hardware, such as a dedicated server or cloud infrastructure, to support the software’s operations.
Potential ROI
RMM software can deliver significant ROI through various benefits:
- Reduced IT Downtime: RMM software allows for proactive monitoring of devices and systems, enabling IT teams to identify and resolve issues before they impact users. This reduces downtime, improving user productivity and minimizing business disruptions.
- Improved Security Posture: RMM software offers robust security features, including vulnerability scanning, endpoint protection, and patch management. These features help organizations strengthen their security posture, reducing the risk of cyberattacks and data breaches.
- Enhanced Productivity: RMM software automates routine IT tasks, freeing up IT staff to focus on more strategic initiatives. This increased efficiency can lead to improved productivity and better utilization of IT resources.
- Cost Savings: By automating tasks, reducing downtime, and improving security, RMM software can lead to significant cost savings. For example, fewer incidents require manual intervention, reducing the need for expensive on-site support and minimizing the impact of security breaches.
Cost-Benefit Comparison
The following table provides a general comparison of the costs and benefits of different RMM software options:
| RMM Software Option | Cost Factors | Benefits |
|---|---|---|
| Free/Open-Source | Lower initial cost, but may require more technical expertise and maintenance | Basic monitoring and management capabilities, community support |
| Basic/Entry-Level | Affordable, but limited features and support | Essential monitoring and management tools, suitable for small businesses |
| Mid-Range/Enterprise | Higher cost, but comprehensive features and support | Advanced monitoring, automation, and security features, ideal for larger organizations |
Trends and Future of RMM Software: Remote Monitoring And Management Rmm Software
The RMM software landscape is continuously evolving, driven by advancements in cloud computing, artificial intelligence (AI), and cybersecurity. These trends are reshaping how IT professionals manage and secure their networks, leading to a more proactive and efficient approach to IT operations.
Cloud-Based RMM Solutions
The shift towards cloud-based RMM solutions is a major trend. Cloud-based RMM platforms offer several advantages, including:
- Scalability and Flexibility: Cloud-based RMM solutions are highly scalable, allowing businesses to adjust their resources based on their needs. They also offer flexibility, enabling IT teams to manage devices from anywhere with an internet connection.
- Cost-Effectiveness: Cloud-based RMM solutions can be more cost-effective than traditional on-premises solutions, as they eliminate the need for hardware investments and maintenance.
- Improved Collaboration: Cloud-based RMM platforms facilitate collaboration among IT teams, allowing them to share information and manage tasks more effectively.
“By 2025, over 80% of enterprises will have adopted a cloud-first strategy, with RMM software being a key component of their IT infrastructure.” – Gartner
AI-Powered Automation
AI is transforming the way RMM software operates. AI-powered automation features can:
- Proactive Threat Detection: AI algorithms can analyze network traffic and device behavior to identify potential security threats in real-time. This enables IT teams to take immediate action to mitigate risks and prevent breaches.
- Automated Patch Management: AI can automate the process of patching vulnerabilities, ensuring that devices are always up-to-date and secure. This reduces the risk of exploitation by attackers.
- Predictive Maintenance: AI can analyze device performance data to predict potential hardware failures, allowing IT teams to proactively address issues before they impact operations.
“AI-powered RMM solutions are expected to reduce IT support costs by up to 30% by 2024.” – IDC
RMM Software in Addressing Evolving Security Threats
RMM software plays a critical role in addressing the ever-evolving landscape of cyber threats. As attackers become more sophisticated, RMM solutions are evolving to provide:
- Enhanced Endpoint Security: RMM software now offers advanced endpoint security features, including real-time threat detection, malware prevention, and data loss prevention.
- Vulnerability Management: RMM platforms provide comprehensive vulnerability management capabilities, allowing IT teams to identify and prioritize vulnerabilities across their network.
- Security Incident Response: RMM solutions can automate the incident response process, allowing IT teams to quickly contain and remediate security incidents.
“RMM software is becoming an essential tool for businesses to protect their data and systems from cyberattacks.” – Forrester
RMM Software and Technology Advancements
RMM software is constantly adapting to emerging technologies, such as:
- Internet of Things (IoT): RMM solutions are expanding to manage and secure IoT devices, as the number of connected devices continues to grow.
- Edge Computing: RMM software is being integrated with edge computing platforms to provide real-time monitoring and management of devices at the edge of the network.
- 5G Networks: RMM solutions are evolving to support the high speeds and low latency of 5G networks, enabling faster and more efficient device management.
Choosing the Right RMM Solution
Finding the perfect RMM solution for your organization can feel like searching for a needle in a haystack. With so many options available, it’s essential to have a clear understanding of your needs and a structured approach to evaluating potential vendors. This chapter will provide you with a comprehensive checklist for evaluating different RMM software providers, tips for conducting a thorough vendor evaluation, and a table comparing key features, pricing, and support options of leading RMM software vendors.
Checklist for Evaluating RMM Software Providers
A comprehensive checklist will help you assess whether an RMM solution aligns with your specific requirements. Here are key areas to consider:
- Functionality and Features: Assess the RMM software’s core features and ensure they cater to your organization’s specific needs. For example, consider features like remote access, patch management, endpoint security, vulnerability scanning, and reporting.
- Scalability and Flexibility: Evaluate the RMM solution’s ability to scale with your organization’s growth. Consider its capacity to manage a growing number of devices and users without compromising performance.
- Integration and Compatibility: Ensure the RMM software seamlessly integrates with your existing IT infrastructure and other essential tools. Consider compatibility with your current operating systems, security software, and other IT management systems.
- Security and Compliance: Evaluate the RMM software’s security measures and its compliance with industry standards like HIPAA or GDPR. This is crucial for safeguarding sensitive data and ensuring compliance with regulatory requirements.
- Ease of Use and Administration: Assess the RMM software’s user interface and administrative tools. Look for a solution that is intuitive, user-friendly, and easy to manage, even for non-technical personnel.
- Pricing and Support: Compare pricing models and support options offered by different RMM vendors. Consider factors like subscription fees, per-device pricing, and the level of support included.
- Customer Reviews and Reputation: Research customer reviews and ratings to understand the vendor’s reputation and the experiences of other users. Look for feedback on features, reliability, and customer support.
- Vendor Stability and Roadmap: Assess the vendor’s financial stability, track record, and future roadmap. Consider their commitment to innovation and continuous improvement.
Tips for Conducting a Thorough Vendor Evaluation
Once you have a checklist in place, follow these tips to ensure a thorough vendor evaluation:
- Request Demonstrations: Request live demonstrations from shortlisted vendors to see the RMM software in action and assess its usability and functionality.
- Ask Detailed Questions: Prepare a list of specific questions to ask vendors during demonstrations or meetings. This will help you gather detailed information about their solutions and how they address your specific requirements.
- Conduct Proof of Concept (POC): Consider conducting a proof of concept (POC) to test the RMM software in a real-world environment. This will help you evaluate its performance, reliability, and integration with your existing infrastructure.
- Negotiate Contract Terms: Carefully review the contract terms and conditions before signing any agreements. Ensure the terms are clear, transparent, and align with your organization’s needs.
Comparing Leading RMM Software Vendors
Here’s a table comparing key features, pricing, and support options of some leading RMM software vendors:
| Vendor | Key Features | Pricing | Support Options |
|---|---|---|---|
| Atera | Remote access, patch management, endpoint security, vulnerability scanning, reporting | Starts at $79 per month for up to 10 devices | 24/7 phone, email, and chat support |
| ConnectWise Automate | Remote access, patch management, endpoint security, vulnerability scanning, reporting, scripting | Starts at $59 per month for up to 10 devices | 24/7 phone, email, and chat support, online resources |
| Datto RMM | Remote access, patch management, endpoint security, vulnerability scanning, reporting, backup and disaster recovery | Starts at $129 per month for up to 10 devices | 24/7 phone, email, and chat support, online resources, training |
| NinjaOne | Remote access, patch management, endpoint security, vulnerability scanning, reporting, scripting | Starts at $69 per month for up to 10 devices | 24/7 phone, email, and chat support, online resources, training |
| SolarWinds N-central | Remote access, patch management, endpoint security, vulnerability scanning, reporting, scripting, automation | Starts at $149 per month for up to 10 devices | 24/7 phone, email, and chat support, online resources, training |
Remember that the best RMM solution for your organization will depend on your specific needs and budget. It’s essential to conduct thorough research, compare options, and choose a solution that aligns with your requirements.
RMM Software for Small and Medium Businesses (SMBs)
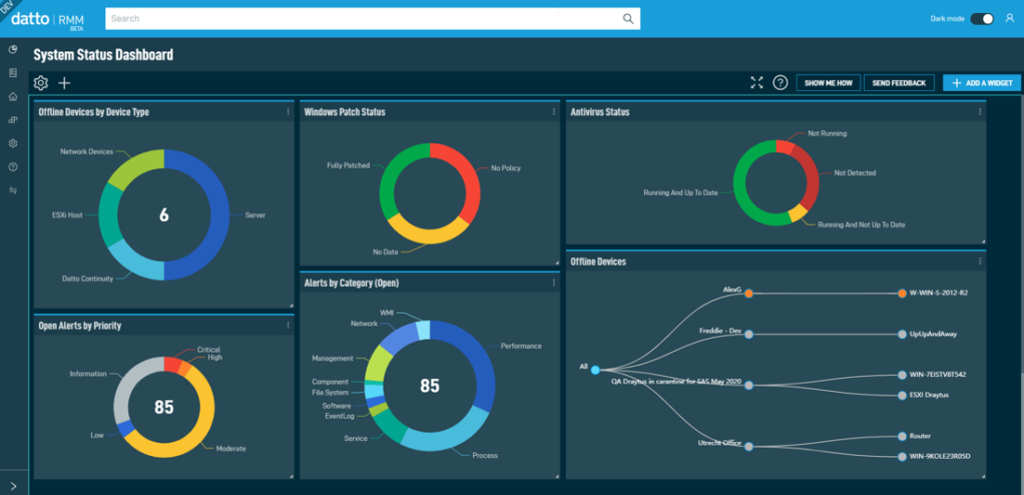
RMM software is particularly beneficial for SMBs, which often have limited IT resources and budgets. These solutions offer a cost-effective way to manage IT infrastructure, improve security, and enhance productivity.
Empowering SMBs with Efficient IT Management
RMM solutions can significantly empower SMBs by providing centralized control over their IT infrastructure, allowing them to manage their systems effectively and cost-efficiently.
- Remote Monitoring and Management: RMM software enables IT professionals to monitor and manage devices remotely, regardless of their physical location. This eliminates the need for on-site visits, saving time and resources. For example, an IT technician can remotely diagnose and fix issues on a server located in a different city without traveling.
- Automated Patch Management: RMM software automates the process of applying software updates and security patches, ensuring that systems are always up-to-date and protected from vulnerabilities. This helps reduce the risk of security breaches and downtime.
- Improved Security Posture: RMM solutions provide comprehensive security features, including endpoint protection, firewall management, and intrusion detection. This helps SMBs strengthen their security posture and mitigate potential threats.
- Proactive Maintenance: RMM software allows for proactive monitoring of system health, enabling early detection and resolution of issues before they impact operations. This reduces downtime and improves overall system reliability.
- Cost Savings: RMM solutions can significantly reduce IT costs by automating tasks, minimizing downtime, and improving efficiency. This allows SMBs to allocate their IT resources more effectively and focus on strategic initiatives.
Examples of RMM Software for SMBs, Remote monitoring and management rmm software
Several RMM software solutions are specifically designed to meet the needs of small and medium businesses. These solutions offer a range of features and pricing options to cater to different business requirements.
- Atera: Atera is a cloud-based RMM platform that provides comprehensive monitoring, management, and automation capabilities. It is designed for MSPs and SMBs and offers features such as remote access, patch management, and security monitoring. Atera’s pricing starts at $79 per month for the “Growth” plan.
- ConnectWise Manage: ConnectWise Manage is a comprehensive RMM solution that provides a wide range of features, including ticketing, billing, and reporting. It is a popular choice for MSPs and SMBs with more complex IT environments. ConnectWise Manage’s pricing is based on the number of devices managed and starts at $1,495 per month for the “Essentials” plan.
- Datto RMM: Datto RMM is a cloud-based RMM solution that focuses on providing comprehensive security and management capabilities. It is a good option for SMBs that prioritize data protection and security. Datto RMM’s pricing starts at $50 per month for the “Essentials” plan.
- NinjaOne: NinjaOne is a cloud-based RMM solution that offers a range of features, including remote access, patch management, and endpoint protection. It is designed for MSPs and SMBs and offers a flexible pricing model based on the number of devices managed. NinjaOne’s pricing starts at $15 per month for the “Starter” plan.
Summary
In conclusion, remote monitoring and management (RMM) software has revolutionized the way businesses approach IT management. By embracing RMM solutions, organizations can unlock significant benefits, including improved efficiency, enhanced security, reduced downtime, and a more proactive approach to IT operations. As technology continues to evolve, RMM software will undoubtedly play an even more critical role in shaping the future of IT management, empowering businesses to adapt and thrive in the digital landscape.
Remote monitoring and management (RMM) software simplifies the process of managing IT infrastructure remotely, enabling proactive maintenance and issue resolution. If you’re looking for a comprehensive solution that includes features like network monitoring, asset management, and security updates, consider kvr software.
KVR software provides a robust platform for managing your IT environment, ensuring smooth operations and reducing downtime.
