Middleware sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset.
Table of Contents
Imagine a world where applications seamlessly communicate, share data, and work together harmoniously. This is the promise of middleware, a vital layer of software that acts as the invisible glue connecting diverse systems and enabling them to interact effortlessly. From facilitating communication between different platforms to enhancing security and performance, middleware plays a crucial role in modern software development.
Middleware Architecture
Middleware solutions are characterized by their layered architecture, designed to facilitate communication and interaction between different applications and systems. This architecture involves a set of components working together to provide a cohesive and efficient environment for data exchange, resource management, and application integration.
Components and Interaction
Middleware architectures typically consist of several components, each playing a crucial role in facilitating communication and data flow. Here’s a breakdown of common components and their interactions:
- Message Queues: These components act as temporary storage for messages exchanged between applications. They enable asynchronous communication, allowing applications to send and receive messages independently, without blocking each other. Applications send messages to queues and retrieve them later, ensuring reliable and efficient data exchange.
- Service Bus: This component serves as a central hub for message routing and management. It acts as a mediator between applications, facilitating communication and ensuring consistent message delivery. The service bus can handle message transformations, security, and other essential functions, simplifying application integration and communication.
- Data Access Layer: This component provides a standardized interface for applications to access and manipulate data stored in various databases and data sources. It abstracts the underlying data storage mechanisms, allowing applications to interact with data sources uniformly, regardless of the specific database technology used.
- Application Servers: These components provide a runtime environment for applications, managing their execution, resources, and interactions with other components. They handle tasks such as resource allocation, security management, and application lifecycle management, ensuring reliable and efficient application execution.
Common Middleware Architectures
Middleware architectures can be classified based on their specific features and functionalities. Here’s a table summarizing common middleware architectures and their key features:
| Architecture | Key Features | Example |
|---|---|---|
| Message-Oriented Middleware (MOM) | Asynchronous communication, message queues, reliable delivery, and message persistence. | RabbitMQ, Apache Kafka, ActiveMQ |
| Enterprise Service Bus (ESB) | Centralized message routing, service orchestration, transformation, and data integration. | Mule ESB, Apache Camel, WSO2 ESB |
| Remote Procedure Call (RPC) | Synchronous communication, procedure calls across networks, and distributed applications. | gRPC, Apache Thrift, Apache Avro |
| Web Services | Standardized communication protocols (SOAP, REST), platform-independent interactions, and distributed applications. | Apache Axis, Apache CXF, Spring Boot |
Middleware Security Considerations
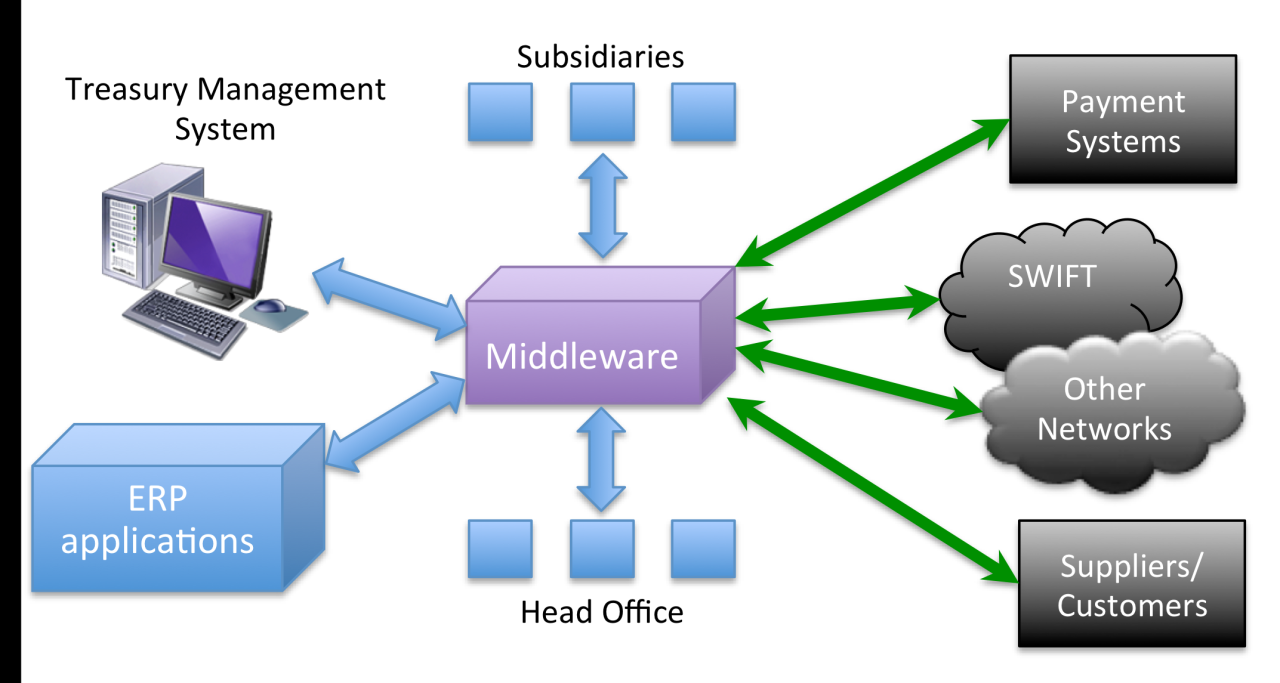
Middleware plays a crucial role in connecting different software components, making applications more flexible and scalable. However, this central position also makes it a prime target for security threats.
Security Challenges Associated with Middleware
Middleware can introduce several security vulnerabilities due to its complex nature and the many interactions it manages. These challenges include:
- Data breaches: Middleware often handles sensitive data, making it a target for attackers seeking to steal or compromise information. This can be exacerbated by poorly configured security settings or outdated software.
- Denial-of-service attacks: Middleware can be overwhelmed by malicious traffic, making it unavailable to legitimate users. This can be achieved through flooding the system with requests or exploiting vulnerabilities in the middleware’s architecture.
- Unauthorized access: Attackers may attempt to gain unauthorized access to middleware components, potentially allowing them to manipulate data, launch further attacks, or gain control of the entire system.
- Misconfiguration: Improperly configured middleware can expose vulnerabilities that attackers can exploit. This can include weak passwords, open ports, or insufficient authentication mechanisms.
- Outdated software: Outdated middleware versions may contain known security vulnerabilities that attackers can exploit. Regularly updating middleware is crucial to mitigate these risks.
Securing Middleware Against Threats
Securing middleware is essential to protect against various threats. This involves implementing a multi-layered approach that considers both technical and organizational aspects.
Data Breaches
To prevent data breaches, it is crucial to implement robust security measures to protect sensitive data.
- Data encryption: Encrypting data in transit and at rest is crucial to prevent unauthorized access. This ensures that even if data is intercepted, it cannot be read or understood.
- Access control: Implementing strong access control mechanisms ensures that only authorized users can access sensitive data. This involves defining roles and permissions based on user needs and minimizing the number of users with administrative privileges.
- Data masking: This technique involves replacing sensitive data with random or meaningless characters, making it unusable for attackers. This can be particularly useful for data used in testing or development environments.
- Regular security audits: Performing regular security audits helps identify vulnerabilities and misconfigurations that could lead to data breaches. These audits should involve both technical and non-technical aspects, such as user access policies and data handling practices.
Denial-of-Service Attacks
Denial-of-service attacks aim to disrupt the availability of middleware by overwhelming it with malicious traffic.
- Rate limiting: Implementing rate limiting mechanisms helps prevent attackers from flooding the middleware with excessive requests. This involves setting limits on the number of requests allowed from a single source within a specific time frame.
- Load balancing: Distributing traffic across multiple servers can help prevent a single server from being overwhelmed by malicious traffic. This also provides redundancy, ensuring that the middleware remains available even if one server fails.
- Intrusion detection and prevention systems (IDS/IPS): These systems monitor network traffic for suspicious activity and can block or mitigate malicious attacks before they impact the middleware. They can detect and block known attack patterns and can be customized to identify unusual traffic patterns.
Unauthorized Access
Preventing unauthorized access to middleware is crucial to maintain the integrity and confidentiality of data and applications.
- Strong authentication: Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), helps verify the identity of users before granting access to middleware components. MFA typically involves requiring users to provide multiple forms of identification, such as a password and a one-time code generated by a mobile app.
- Authorization: Once authenticated, users should only be granted access to the resources they need to perform their tasks. This involves defining roles and permissions based on user responsibilities and ensuring that users can only access the data and applications they are authorized to use.
- Least privilege principle: This principle states that users should only be granted the minimum privileges necessary to perform their tasks. This helps to minimize the impact of compromised accounts, as attackers with limited privileges can only access a restricted set of resources.
Popular Middleware Technologies
Middleware technologies play a crucial role in modern software development, acting as a bridge between applications and underlying infrastructure. They simplify application development, enhance performance, and improve security. This section will explore some of the most popular middleware technologies available in the market, comparing and contrasting their features, strengths, and limitations.
Popular Middleware Technologies
- Message Queues: Message queues, such as RabbitMQ, Apache Kafka, and Amazon SQS, facilitate asynchronous communication between applications. They provide a robust mechanism for decoupling applications, enabling them to communicate independently and handle events efficiently.
- API Gateways: API gateways, like Tyk, Kong, and AWS API Gateway, act as central control points for managing API traffic. They provide features such as rate limiting, authentication, authorization, and request routing, ensuring secure and efficient API access.
- Service Bus: Service buses, such as Azure Service Bus, Red Hat Fuse, and MuleSoft, offer enterprise-grade messaging and integration capabilities. They provide features for reliable messaging, message transformation, and integration with various systems, simplifying complex application integrations.
- Caching Servers: Caching servers, like Redis, Memcached, and Couchbase, improve application performance by storing frequently accessed data in memory. They reduce database load and latency, resulting in faster response times and improved user experience.
- Enterprise Service Bus (ESB): ESBs, such as Oracle Service Bus, IBM WebSphere Message Broker, and Tibco BusinessWorks, provide a comprehensive platform for connecting and managing various applications and services. They offer features like message routing, transformation, and orchestration, enabling complex business process automation.
- Application Servers: Application servers, like JBoss, WebSphere, and WebLogic, provide runtime environments for deploying and managing web applications. They offer features like container management, security, and transaction management, ensuring reliable and scalable application execution.
Comparison of Middleware Technologies
| Middleware Technology | Vendor | Strengths | Limitations |
|---|---|---|---|
| RabbitMQ | VMware | High performance, reliability, and scalability | Complex configuration, limited integration with other technologies |
| Apache Kafka | Apache Software Foundation | High throughput, fault tolerance, and stream processing capabilities | Requires specialized expertise, limited support for complex business processes |
| Amazon SQS | Amazon Web Services | Scalable, reliable, and fully managed service | Limited control over message delivery, vendor lock-in |
| Tyk | Tyk Technologies | Open source, flexible, and extensible | Limited enterprise features, requires expertise in API management |
| Kong | Kong Inc. | Lightweight, high performance, and easy to use | Limited integration with some enterprise systems, requires some technical expertise |
| AWS API Gateway | Amazon Web Services | Scalable, secure, and fully managed service | Vendor lock-in, limited customization options |
| Azure Service Bus | Microsoft | Reliable, scalable, and integrated with Azure services | Vendor lock-in, limited support for open source technologies |
| Red Hat Fuse | Red Hat | Open source, comprehensive integration capabilities, and support for various protocols | Requires expertise in Java and integration technologies, complex configuration |
| MuleSoft | MuleSoft | Easy to use, visual development environment, and extensive connectors | Proprietary platform, expensive for large-scale deployments |
| Redis | Redis Labs | Fast, flexible, and supports various data structures | Limited persistence options, requires expertise in Redis |
| Memcached | Danga Interactive | Simple, fast, and widely used | Limited data structures, no persistence options |
| Couchbase | Couchbase | Scalable, distributed, and supports NoSQL data models | Complex configuration, requires expertise in NoSQL databases |
| Oracle Service Bus | Oracle | Enterprise-grade, comprehensive integration capabilities, and support for various protocols | Expensive, complex to manage, and requires specialized expertise |
| IBM WebSphere Message Broker | IBM | Reliable, scalable, and supports various messaging protocols | Expensive, requires specialized expertise, and vendor lock-in |
| Tibco BusinessWorks | TIBCO Software | Comprehensive integration capabilities, visual development environment, and support for various protocols | Expensive, complex to manage, and requires specialized expertise |
| JBoss | Red Hat | Open source, lightweight, and supports various Java EE specifications | Limited support for non-Java technologies, requires some technical expertise |
| WebSphere | IBM | Enterprise-grade, supports various Java EE specifications, and offers comprehensive management tools | Expensive, requires specialized expertise, and vendor lock-in |
| WebLogic | Oracle | High performance, supports various Java EE specifications, and offers comprehensive management tools | Expensive, requires specialized expertise, and vendor lock-in |
Middleware Trends and Future Directions
The middleware landscape is continuously evolving, driven by technological advancements and changing demands in application development. This evolution is shaping the way middleware is designed, deployed, and utilized. This section explores some key trends and future directions in the middleware domain.
Impact of AI on Middleware
AI is transforming various aspects of software development, and middleware is no exception. AI-powered middleware is becoming increasingly prevalent, offering several advantages:
- Intelligent Routing and Load Balancing: AI algorithms can analyze real-time data and traffic patterns to optimize routing and load balancing, ensuring efficient resource utilization and improved application performance. This dynamic adaptation to changing conditions leads to better resource allocation and a more responsive application environment.
- Automated Configuration and Management: AI-driven middleware can automate configuration tasks, reducing manual effort and minimizing human errors. By analyzing application behavior and system logs, AI can automatically adjust configurations to optimize performance and security. This automation simplifies management and ensures consistency across different environments.
- Enhanced Security: AI can be used to detect and respond to security threats in real-time. Machine learning algorithms can identify suspicious patterns in network traffic and user behavior, helping to prevent attacks and protect sensitive data. This proactive approach enhances the security posture of applications and middleware systems.
Blockchain’s Role in Middleware
Blockchain technology, known for its decentralized and immutable nature, is emerging as a transformative force in middleware development. Blockchain-based middleware offers unique capabilities:
- Secure and Transparent Data Sharing: Blockchain provides a secure and transparent platform for data sharing between applications and systems. This eliminates the need for centralized trust and ensures data integrity, enhancing collaboration and interoperability. This trustless environment enables secure data exchange without relying on intermediaries.
- Decentralized Microservices Architecture: Blockchain can facilitate the development of decentralized microservices architectures, where individual services operate independently and communicate securely over a distributed ledger. This approach increases resilience and scalability, as failures in one service do not affect the overall system.
- Improved Auditability and Traceability: Blockchain’s immutability ensures that all transactions and events are permanently recorded and auditable. This transparency enhances accountability and simplifies troubleshooting by providing a complete history of interactions. This immutability ensures data integrity and provides a verifiable audit trail for all transactions.
Edge Computing and Middleware
Edge computing, where data processing occurs closer to the source, is gaining traction, particularly in applications requiring low latency and high bandwidth. Middleware plays a crucial role in edge environments:
- Edge-Optimized Middleware: Middleware solutions specifically designed for edge environments are emerging, offering features like reduced resource footprint, optimized communication protocols, and enhanced security. This specialized middleware addresses the unique challenges of edge computing, such as limited resources and unreliable connectivity.
- Distributed Data Management: Edge computing requires efficient data management at the edge. Middleware can facilitate distributed data storage and processing, enabling real-time analysis and decision-making without relying on centralized servers. This decentralized approach enhances data locality and reduces latency.
- Enhanced Scalability and Resilience: By distributing processing and data management across multiple edge nodes, middleware contributes to increased scalability and resilience. This distributed architecture can handle peak workloads and withstand failures in individual nodes, ensuring continuous operation. This distributed architecture provides fault tolerance and scalability for edge deployments.
Final Review
As we delve deeper into the world of middleware, we discover a powerful and versatile tool that empowers developers to build robust, scalable, and secure applications. By understanding the principles, benefits, and challenges associated with middleware, we can unlock its full potential and create innovative solutions that address the ever-evolving needs of the digital landscape.
Middleware acts as a bridge between different software components, allowing them to communicate and work together seamlessly. A great example of middleware in action is easeus partition master free , a tool that allows you to manage and modify hard drive partitions without needing to delve into complex system settings.
Middleware, like EaseUS Partition Master, simplifies tasks and allows developers to focus on building the core functionality of their applications.
